
THE FASTEST WAY TO SCALABLE POCUS
One system to connect every device, workflow, and department—Compass AI transforms how health systems scale point-of-care ultrasound, improving efficiency and care quality.
Disconnected systems cost more than you think.
Today’s POCUS programs are a patchwork—departments work in silos, documentation lags, and scans slip through the cracks. Every missed study is a compliance risk.
Most scans go unbilled and nearly 84% slip through the cracks. Close the gap by building compliance directly into your workflow.1
Orders-based workflows slow you down. Compass AI takes you from scan to submission in record time—no orders, fewer clicks, fewer errors, more accountability.2
QA and proficiency are essential, but a burden to manage. Standardize education at scale with automated review, guided feedback, and actionable insight into learner performance.
Practical, purpose-built intelligence in everyday workflows.
Compass AI automates what slows clinicians down—transforming hours of documentation and QA into significantly faster, more efficient workflows.
QA Agent
Automate and speed up QA with AI-powered review and guided feedback. Reduce manual workload, deliver faster learner feedback, and scale education across your program without scaling effort.
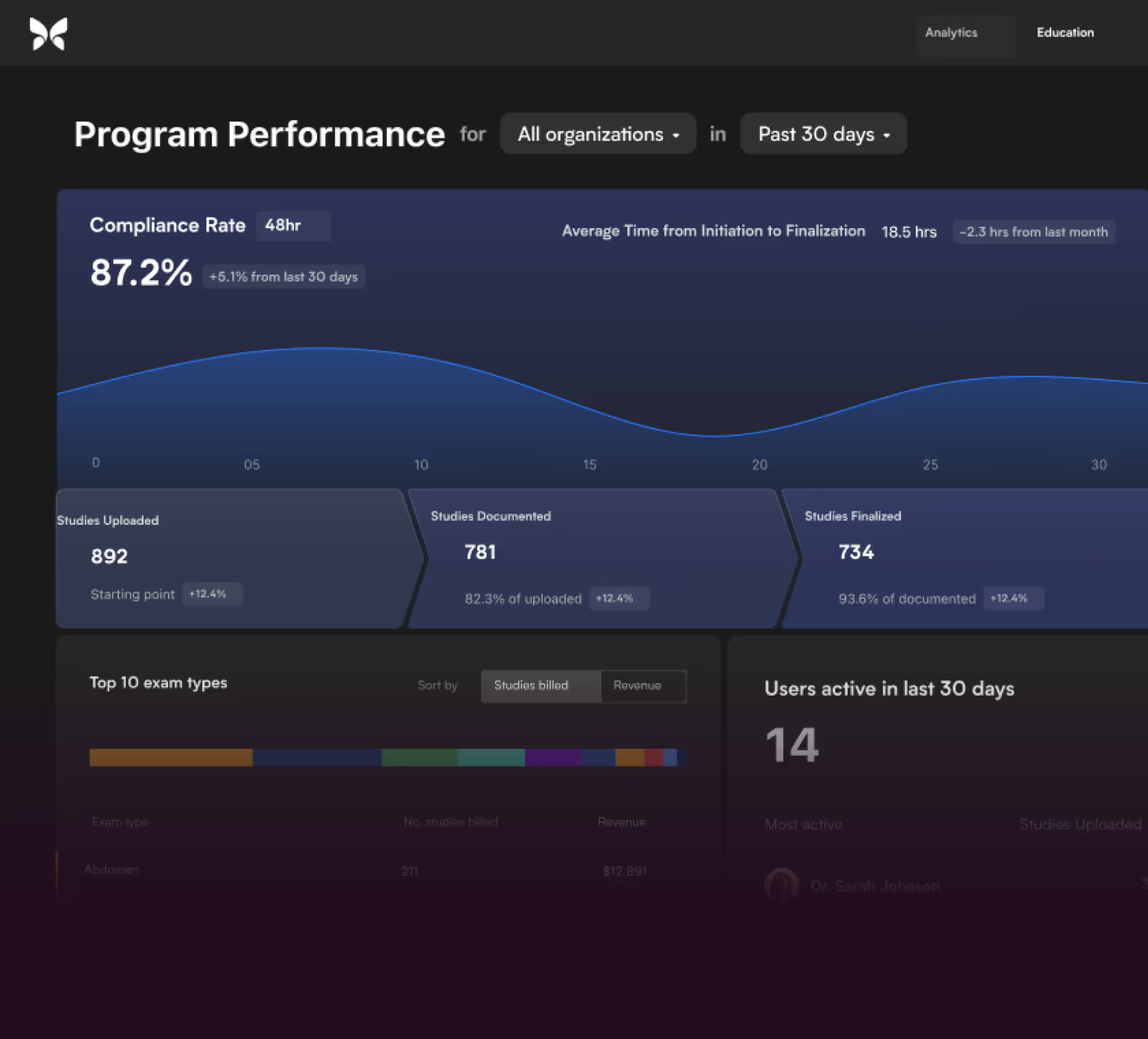
Complete oversight means fewer gaps and confidence that every scan counts. Compass AI gives departments and health systems a centralized, transparent view of all imaging, compliance and proficiency—delivering true clarity at scale.

The future of POCUS starts here
Compass AI is the connective tissue for scalable, enterprise-wide ultrasound—simplifying workflows, unlocking compliance, and turning every scan into actionable insight to deliver better care.
1,2. Rong K, Chimileski B, Kaloudis P, Herbst MK. Impact of an epic-integrated point-of-care ultrasound workflow on ultrasound performance, compliance, and potential revenue. Am J Emerg Med. 2021;49:233-239. doi:10.1016/j.ajem.2021.06.009




